Account Takeover Fraud , Active Defense & Deception , Application Security
Zynga's Breach Notification: How Not to Inform Victims
Don't Blame Us, Blame Hackers, Mobile Gaming Giant Says
"Cyberattacks are one of the unfortunate realities of doing business today," reads a data breach notification issued by San Francisco-based mobile gaming company Zynga. In other words: Everyone gets hacked, what could we have done?
Zynga manages to overlook the first rule of crisis management: Own your mistakes. Because it's the rare - as in nonexistent - site that boasts 100 percent hacker-proof systems.
How much a company budgets for security, including recruiting and retaining top talent, as well as what types of data they opt to store and how, remains in no small part a business decision.
But instead of issuing at least a partial mea culpa, the gaming firm behind such hits as FarmVille and Zynga Poker, and which counts more than 1 billion users of its games worldwide, opts for deflection.
"Cyberattacks are one of the unfortunate realities of doing business today," the company's initial September 12 data breach notification begins. "We recently discovered that certain player account information may have been illegally accessed by outside hackers. An investigation was immediately commenced, leading third-party forensics firms were retained to assist, and we have contacted law enforcement."
Zynga repeated that announcement in an updated breach notification issued on Tuesday. And, of course, it includes the unfortunate reality - as in seemingly inevitable, clichéd, and now totally meaningless - that is the following data breach notification boilerplate: "The security of our player data is extremely important to us."
"Was the breach really an 'unfortunate reality'?" asks data breach expert Troy Hunt, creator of the free Have I Been Pwned breach-notification service. "Or was it due to bad code / config somewhere?"
Geez @zynga, starting a data breach notification with "Cyber attacks are one of the unfortunate realities of doing business today" really doesn't read well. Was the breach really an "unfortunate reality"? Or was it due to bad code / config somewhere?https://t.co/yz7VVZR6ax
— Troy Hunt (@troyhunt) October 1, 2019
As The Hacker News first reported on Sunday, the prolific Pakistani hacker who goes by "Gnosticplayers" claims to have perpetrated the hack attack, resulting in the theft of customer account information for more than 218 million users of "Words With Friends," a popular multiplayer word game that plays similar to the classic board game Scrabble.
Zynga said that it does not believe that any financial information was stolen. "However, we understand that account information for certain players of certain Zynga games may have been accessed," it says. "As a precaution, we have taken steps to protect certain players' accounts from invalid logins, including but not limited to where we believe that passwords may have been accessed."
Teardown: Zynga's Breach Notification
Several points from Zynga's breach notification immediately jump out:
- Security: The company makes no mention of the defenses it has in place that might have blunted the "unfortunate reality" - of which it should have been well aware - that it would be targeted by hackers.
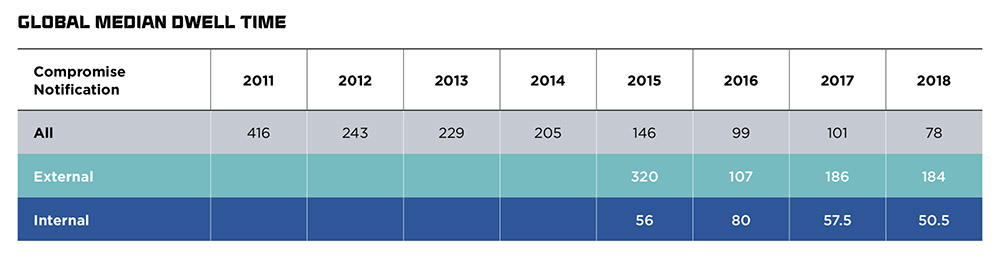
- Discovery: The breach notification suggests that Zynga itself didn't initially identify the data theft, but was rather informed of it by a third party. This is not unusual. According to cybersecurity firm FireEye's latest Mandiant M-Trends report, for investigations conducted by the firm's incident response teams in 2018, 41 percent of breach victims first learned they'd been breached from an external source, rather than discovering the intrusion themselves.
- Law enforcement: Breached organizations inevitably note that they've alerted law enforcement to the breach. While this might offer a feel-good factor - "underestimate the long arm of the law at your peril" and so on - and eventually lead to arrests, it does nothing to fix the fact that people's personal information was exposed and may have already been used against them.
- Passwords: As a result of the breach, one no-brainer best practice for all Zynga users would be to change their password, and ensure that they're not reusing the potentially compromised password for any site or service. Otherwise, they're easy prey for credential-stuffing attacks. Zynga, however, notably stops short of recommending that everyone change their password.
- Third-party investigators: On the other hand, kudos to Zynga for working with outside digital forensic investigators to investigate the breach. While this is de rigueur for breached businesses, it's still important to emphasize that after an intrusion, few firms will have the in-house incident response expertise they require to investigate, scrub the environment and prevent repeat attacks from occurring.
A Zynga spokeswoman declined to comment on when and how the breach happened, when and how it was discovered, and how the company secures passwords.
Gnosticplayers Strikes Again
But Gnosticplayers told Hacker News that compromised Zynga information included:
- Usernames;
- Email addresses;
- Zynga login ID;
- "Hashed passwords, SHA1 with salt";
- Password reset tokens, if they had been previously requested;
- Phone numbers, if provided by a user;
- Facebook ID, if provided by a user;
- Zynga account ID.
Gnosticplayers' suggestion that the stolen passwords were hashed using SHA1 - even with salt - is concerning. Security experts have long warned that SHA1 is not fit for protecting passwords because it's so easy to crack. As a result, any organization that continues to use SHA1 should be viewed as having substandard security practices in place, and by extension not taking seriously the security of its customer data (see: Party Like Every Day Is World Password Day).
When Zynga was breached remains unclear, but the intrusion could have happened weeks or months before it came to light. Indeed, the average time it takes for an organization to discover an intrusion, when it first learns of the intrusion from an external source - such as the FBI, a security researcher or journalist - is 184 days, according to FireEye's Mandiant.
The Hacker News reports that GnosticPlayers has form for hacking websites, grabbing data and offering it for sale online in exchange for bitcoins. Earlier this year, the hacker was advertising nearly 1 billion stolen account details online, in part via the now-defunct Dream Market, purportedly obtained from such sites and services as Dubsmash, MyFitnessPal and MyHeritage.
This then is one of today's business realities: Hackers are going to continue targeting customer data. How companies approach information security makes the difference between whether they might suffer an unfortunate data exposure, or rather mitigate breaches by fortunately having put appropriate, cyberattack-repelling defenses and controls in place. Fortune, in other words, favors those who prepare.











