Sponsored by Tata Communications
Sponsored by Tata Communications
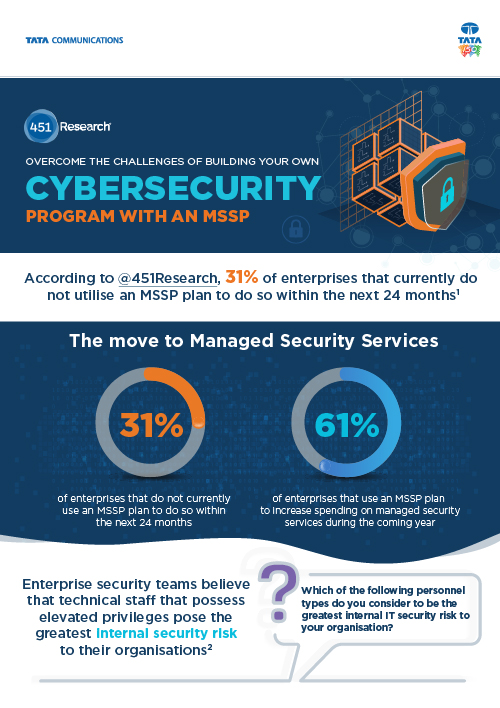
Overcome the challenges of building your own cybersecurity program with an MSSP
Sponsored by Arctic Wolf Networks
A Cybersecurity Risk Checklist for Financial Institutions
Sponsored by Pure Storage
Video Surveillance Data: What's Next?
Sponsored by F5 Networks
The Forrester Wave : Web Application Firewalls
Sponsored by Lastline
A New Look at Email Security: How to Improve Detection of Malicious Payloads
Sponsored by Venafi
Organisations Vulnerable to Insider and Cyber Threats: Misuse of SSH Keys
Sponsored by Venafi
Stop Abuse of Privileged Access: Protect your Organisation's SSH Keys
Sponsored by Venafi
The Machine Identity Crisis in the UK and EU
Sponsored by Venafi
Machine Identity for Dummies eBook: Protecting UK and EU Organisations
Sponsored by Ping Identity
The Power of Identity in Financial Services
Sponsored by Acronis